Real-time Transparency
Every detail of our testing is available to the client, during testing, in real-time.
This allows our client to track progress during testing, SOC staff to correlate recent activity to our testing (vs. a possible unauthorized attacker), IT staff to review any configuration changes made, and security staff to know about vulnerabilities they should start working to fixing immediately (vs. waiting for the report). It also enables every test we perform to be a Purple Team approach if the client chooses to. You can read more about Purple Teaming here.
We relay information in the following ways during testing:
- Secure communications and file transfer avenues to ensure your information remains protected
- Immediate notification if an imminent risk or compromise is identified
- 24-7 support – name, phone number, and email address of all security engineers performing tests
- Real-time notes, a journal-style timeline, file sharing, etc.
- Syncs with the blue team (during a purple team approach)
PEN Consultants provides real-time access to everything we have done, are doing, or plan to do; down to the tool and command level:
- security engineers’ real-time, unedited, unfiltered notes about where they currently are in the testing process
- individual tests completed, what has already been tested/attacked
- current tests being carried out
- upcoming tests yet to be performed
- full commands ran for all tools and utilities
- raw outputs and reports
- exploits used
- vulnerabilities found
- any changes/modifications made (most are pre-coordinated)
- timestamps
- access to any dedicated infrastructure being used (if applicable and requested)
- and more – blue team has access to everything
To further expand on just one of the methods PEN Consultants uses to keep you abreast of the details of testing, here is more information about our real-time notes and journal-style timeline for every major task or simulated attack. You have access to everything we have done, are doing, or plan to do, down to the tool and command level. Each command we run, or tool we use, is timestamped and listed as it is being run. Our “to do” list, “tasks complete” list, and every confirmed vulnerability or finding is also documented in real-time. These live notes are features unique to PEN Consultants since 2014 and have proven to be extremely valuable to many of our clients.
Note: In both cases, these entries are raw notes that would be roughly equivalent to quickly writing on a notepad. Because of this, they are not spell or grammar-checked and will not have all of the details and recommendations listed. Those details, along with a professional report, are provided after testing is complete.
Excerpts from the Live Timeline
[SNIP]
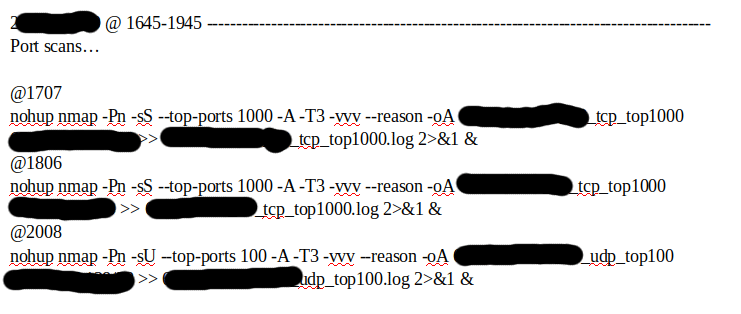
[SNIP]

[SNIP]

[SNIP]
Excerpts from the Live Notes
[SNIP]
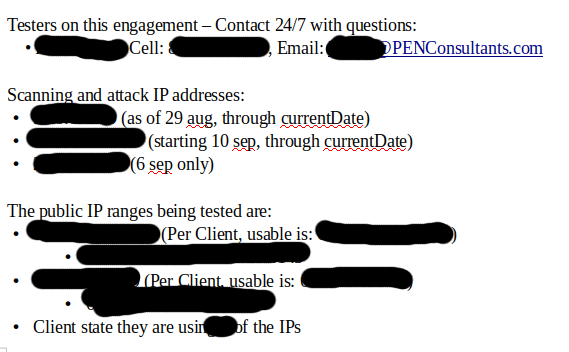
[SNIP]
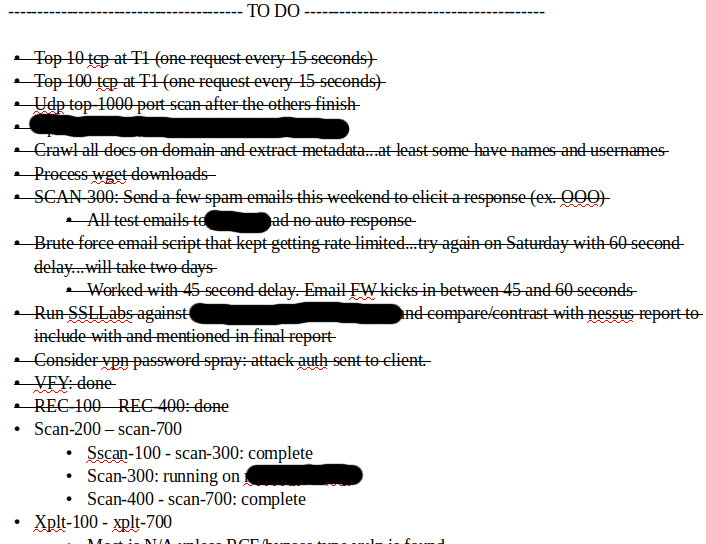
[SNIP]

[SNIP]
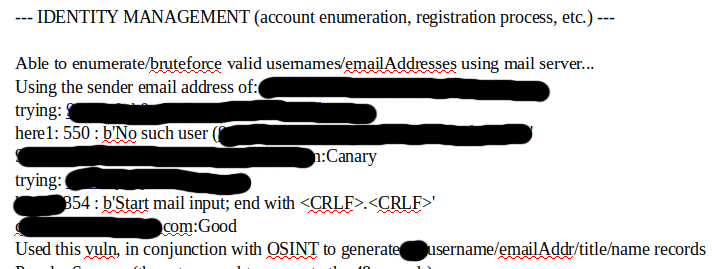
[SNIP]

[SNIP]
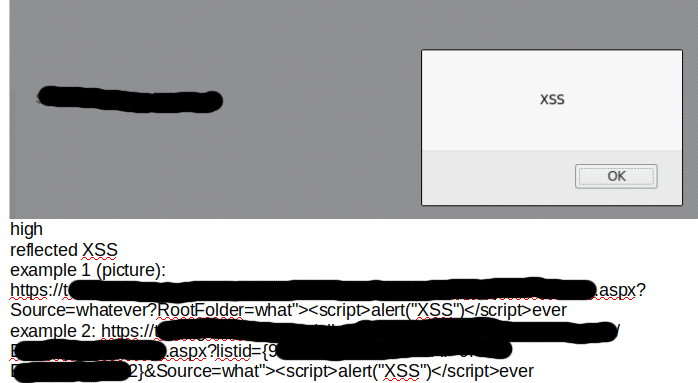
[SNIP] [SNIP]
