A Vulnerability Disclosure Gone Wrong
An example of a vulnerability disclosure gone wrong…
Background
I debated mentioning the company but will resist. While making a contribution through a well-known payment processing app, I discovered a vulnerability. It was an OWASP top-10 vulnerability and was discoverable while doing nothing more than using the app as a normal-ish user would. Okay, true, my wife probably would not have discovered it. But, that’s simply because she would not have known what she was looking for.
My attempt at responsible disclosure
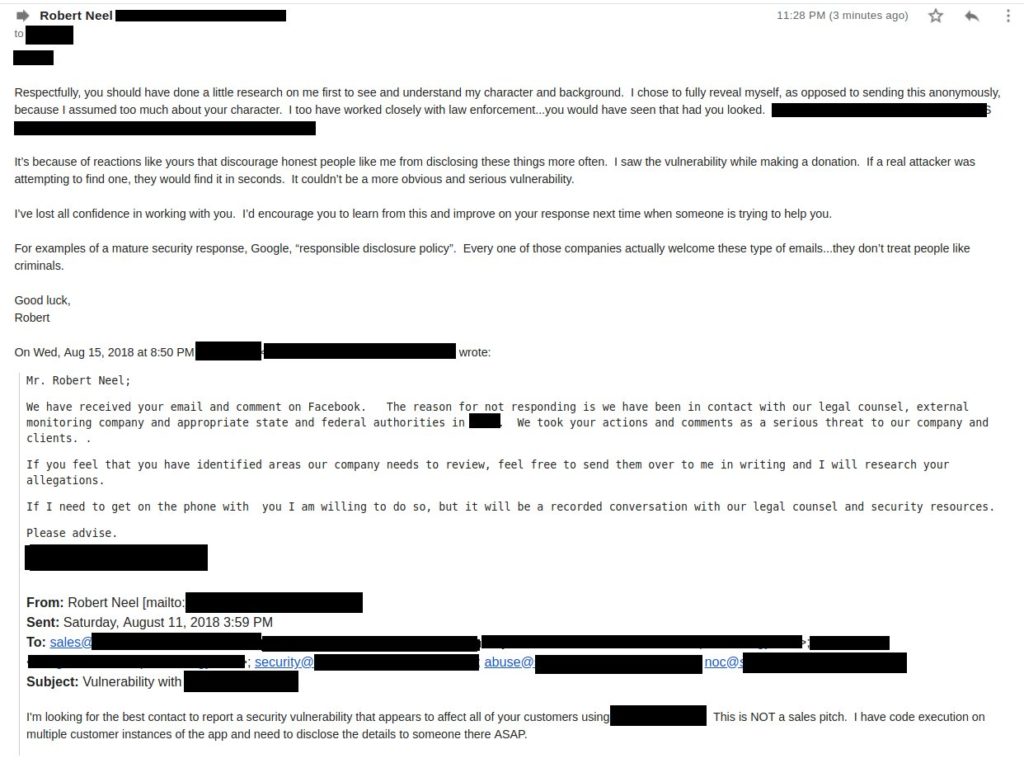
Read the email thread from the bottom up…

InfoSec professionals beware
If an origination does not have a disclosure policy/program/process/contact/etc., do NOT attempt to disclose a discovered vulnerability. There’s nothing to gain, but everything to lose. It’s just not worth it. If the organization is too immature to have a disclosure policy or process, they are likely going to handle a disclosure immaturely as well.
Businesses: Please post a disclosure policy/process
All businesses need to make sure they have created and posted a responsible disclosure process, contact information, and/or listed their org with a bug bounty program. There are so many options and places to do this. Here are a few examples, all taken straight from https://www.owasp.org/index.php/Vulnerability_Disclosure_Cheat_Sheet:
- Create security contacts: typical security@, abuse@, noc@ (RFC2142) or public CERT.
- Create and post a vulnerability disclosure policy/page
- Sign-up with a bug bounty program. Example platforms: HackerOne, bugcrowd, synack, bountyfactory.io…
- Create a security.txt file on your website. More info: https://securitytxt.org/
If you have any doubts on what to do, please reach out to me; I’ll be more than glad to offer assistance. Most of us disclosing vulnerabilities are not “bad” people wanting to cause you harm. We’re here to help make you more secure!
Original Source: https://twitter.com/redeemedHacker/status/1029950560517148672
If you are looking for a reliable and experienced offensive security service that provides Rock Solid Security, look no further than PEN Consultants for all your information and cybersecurity testing needs. Contact us: https://penconsultants.com/contact-us/