What do you call a User Enumeration attack against a login service (i.e. username + password)? Based on recent polling (Source_1, Source_2), it would appear our industry peers call this a password spray attack (by a 3-to-1 margin), despite the purpose clearly being for user enumeration. This article will explain why we are taking a minority […]
Category: Online Security

Building a Security Testing Business
I am often asked, “How did you get started with your security testing business?” “What are some lessons learned?” “What are your current challenges?” I have been asked enough times that I decided to post my thoughts in blog format. How did you decide it was the right time to take the step from W-2 […]

MFA Implementation Attacks
Most Multi-Factor-Authentication (MFA) implementations do not protect your password from brute forcing or from account level DoS attacks. This article will demonstrate various attacks that exploit weaknesses found in nearly every industry Identity and Access Management (IAM) provider/solution as well as offer solutions on how to mitigate. Note: This article builds on the previously released https://penconsultants.com/blog/tips-tricks/mfa-without-the-fud/ […]

Vendor: Protect Your Code and Your Customers
Security through obscurity is no security at all. Obscurity does indeed add an extra level of protection and should not be ignored altogether. When creating an application, a vendor should follow all best practices to protect their application/code from “reverse-engineering, tampering, invasive monitoring, and intrusion” (Source: OWASP.org). OWASP calls this “Application Hardening and Shielding”. Read […]
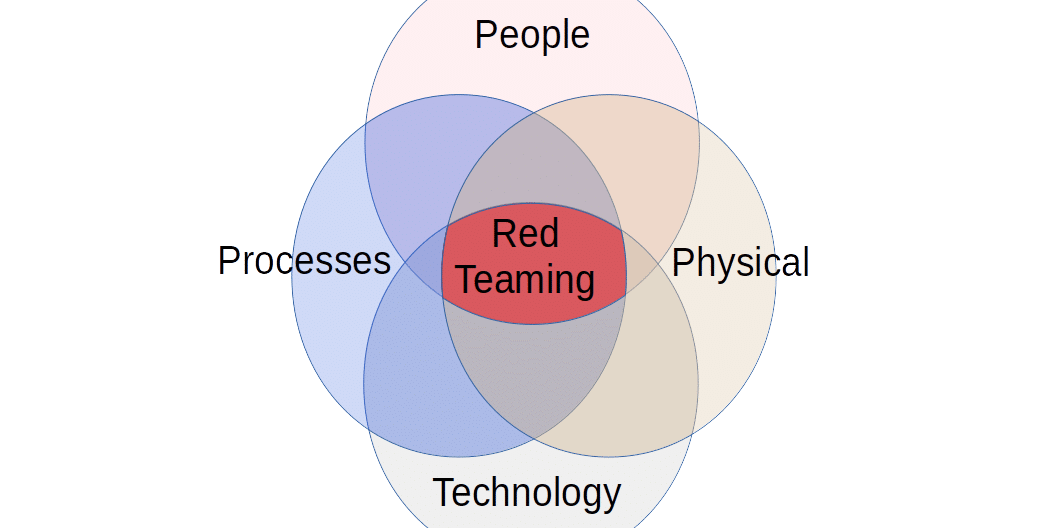
Red Teaming vs Penetration Testing vs Vulnerability Scanning vs Vulnerability Assessments
What is the difference between “Vulnerability Scanning”, “Vulnerability Assessments”, “Penetration Testing”, and “Red Teaming”? What do they mean? Which one do you need performed on your systems? The industry is very opinionated on the definitions of these four terms. This article will share our view of the similarities and differences between vulnerability scanning (vuln scan), […]

Threat Intelligence and Brand Monitoring
One thing that nearly every department in your organization is concerned with is monitoring for references to your organization on the internet, such as brand reputation, cybersecurity threats, intellectual property rights, threats of harm against life or property, etc. But, what are your options? [This is a work in progress in which we intend to […]

Tachyon – A Security Pros Paradise
I recently had the privilege to perform full scope application security testing against 1E’s Tachyon, an endpoint incident response and remediation platform. I was so impressed with it, I sought (and received) approval from 1E to release this article publicly, detailing my impressions. Earlier this year, 1E and I began dialoguing about the possibility of evaluating […]
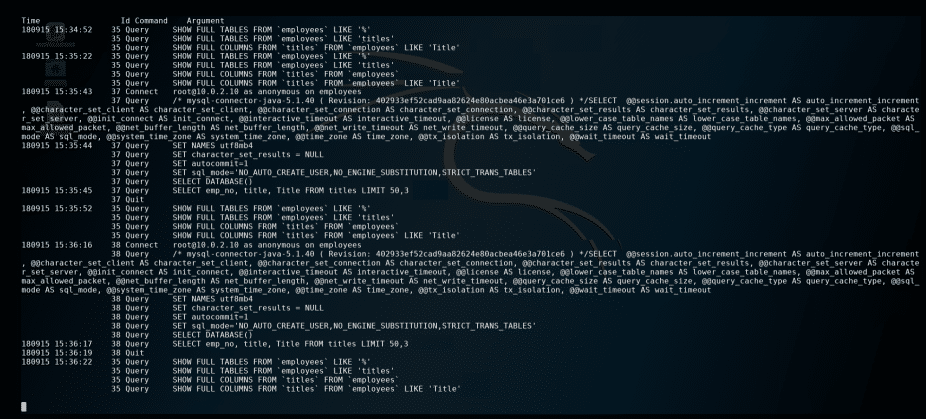
Passwords in DB Logs
This was useful (for an attacker) when password hashing (during authentication) was being performed at the DB level. Background Having access to a DB with encrypted (and salted) password hashes can still present a challenge to recovering a significant percentage of the cleartext passwords. Sure, one will be able to crack some using a decent […]
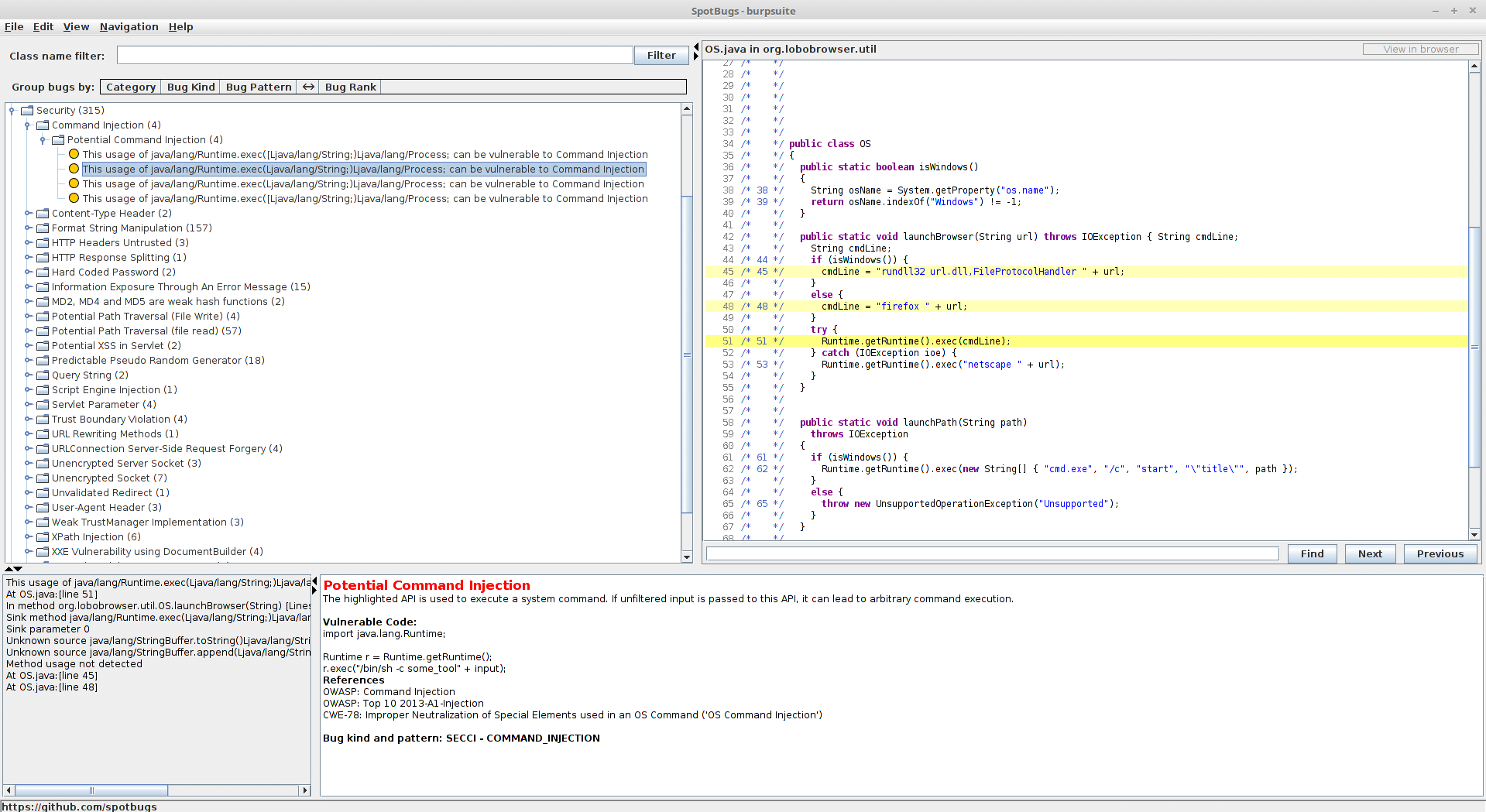
Finding Vulns in JARs with Spotbugs
How to find security vulnerabilities in JARs with SpotBugs… [Note: burpsuite is just being used as an example] Spotbugs is awesome. But, the instructions for compiling it and running as a standalone app were not that clear to me. Because of this, I decided to put together the rather simple steps below. Prerequisites Decompile the […]
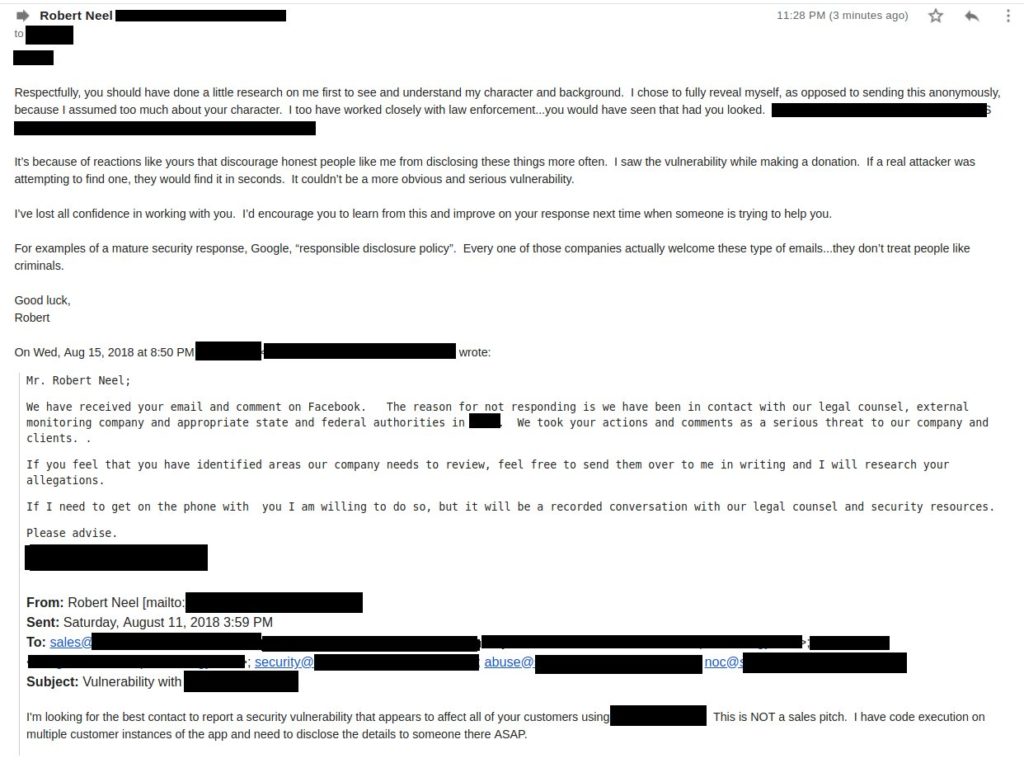
A Vulnerability Disclosure Gone Wrong
An example of a vulnerability disclosure gone wrong… Background I debated mentioning the company but will resist. While making a contribution through a well-known payment processing app, I discovered a vulnerability. It was an OWASP top-10 vulnerability and was discoverable while doing nothing more than using the app as a normal-ish user would. Okay, true, […]

