Finding Vulns in JARs with Spotbugs
How to find security vulnerabilities in JARs with SpotBugs…
[Note: burpsuite is just being used as an example]
Spotbugs is awesome. But, the instructions for compiling it and running as a standalone app were not that clear to me. Because of this, I decided to put together the rather simple steps below.
Prerequisites
Decompile the JAR being analyzed using JD/JD-GUI (or similar). Google it, if needed. There’s a lot of info out there.
Compiling Spotbugs
In Debian/Ubuntu:
wget https://github.com/spotbugs/spotbugs/archive/release-3.1.zip unzip http://release-3.1.zip cd spotbugs-release-3.1 ./gradlew ./gradlew spotbugs:build cp spotbugs/build/distributions/spotbugs-3.1.7-SNAPSHOT.tgz ../. cd .. tar -xvzf spotbugs-3.1.7-SNAPSHOT.tgz
Running Spotbugs
java -jar spotbugs-3.1.7-SNAPSHOT/lib/spotbugs.jar
- File > New Project
- Classpath: [path]/file.jar
- Aux Classpath: add all .jar resources (if needed) for the JAR being analyzed
- Source directories: Folder of decompiled source code…should contain (for example) com, META-INF, etc.
- “OK”

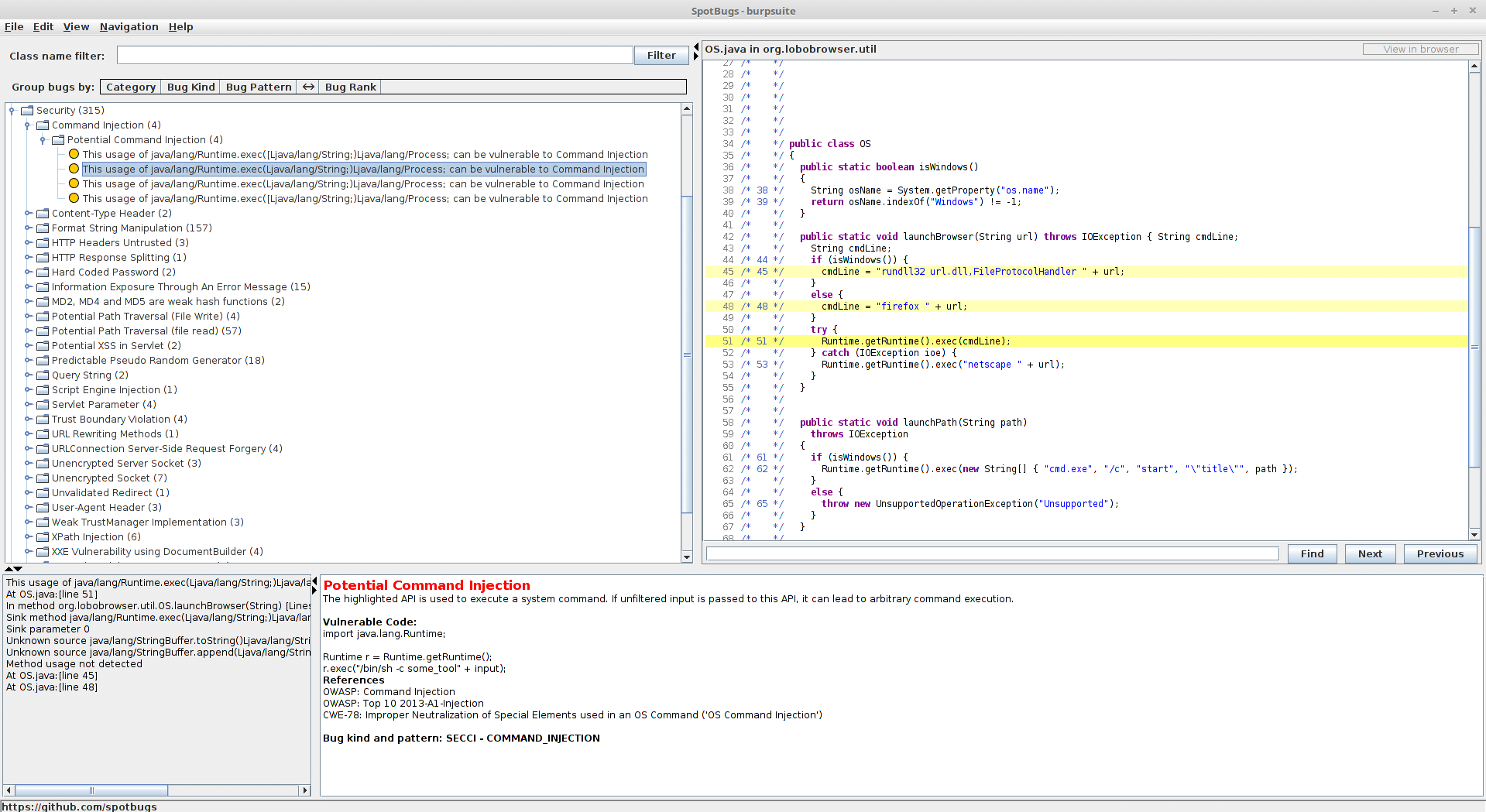
Finding Vulnerabilities
After the above finishes processing, you’ll be presented with a list of possible vulnerabilities (under security) as well as best practice-type findings. I’ve found that there is a high false-positive rate, in terms of exploitable findings. Spotbugs appears to just be performing simple string/regex comparison but does not (due to complexity) actually walk back up the logical flow to determine if a certain finding is actually exploitable. That will be your part :-).
Have fun!

Original Source: https://twitter.com/redeemedHacker/status/1039315054661967872
If you are looking for a reliable and experienced offensive security service that provides Rock Solid Security, look no further than PEN Consultants for all your information and cybersecurity testing needs. Contact us: https://penconsultants.com/contact-us/