Is it acceptable for a male to walk up to a female coworker and say, “You’ve got a booty like a Cadillac”? What about singing, to the same co-worker, “Come to the back seat of my car and I’ll let you have it”? I think most would agree these would not be acceptable. How is […]
Year: 2017

Binary File Patching Scripts
I am releasing code to help attackers patch their binaries on the fly to avoid checksum-based detections. As I mentioned in a previous article, https://penconsultants.com/traditional-iocs-suck/, checksum-based detections are close to worthless. But, they are still used by AV vendors, intel feeds, proxy and endpoint-based detections, etc. Defenders need to stop relying on checksum-based detections. I’m releasing […]
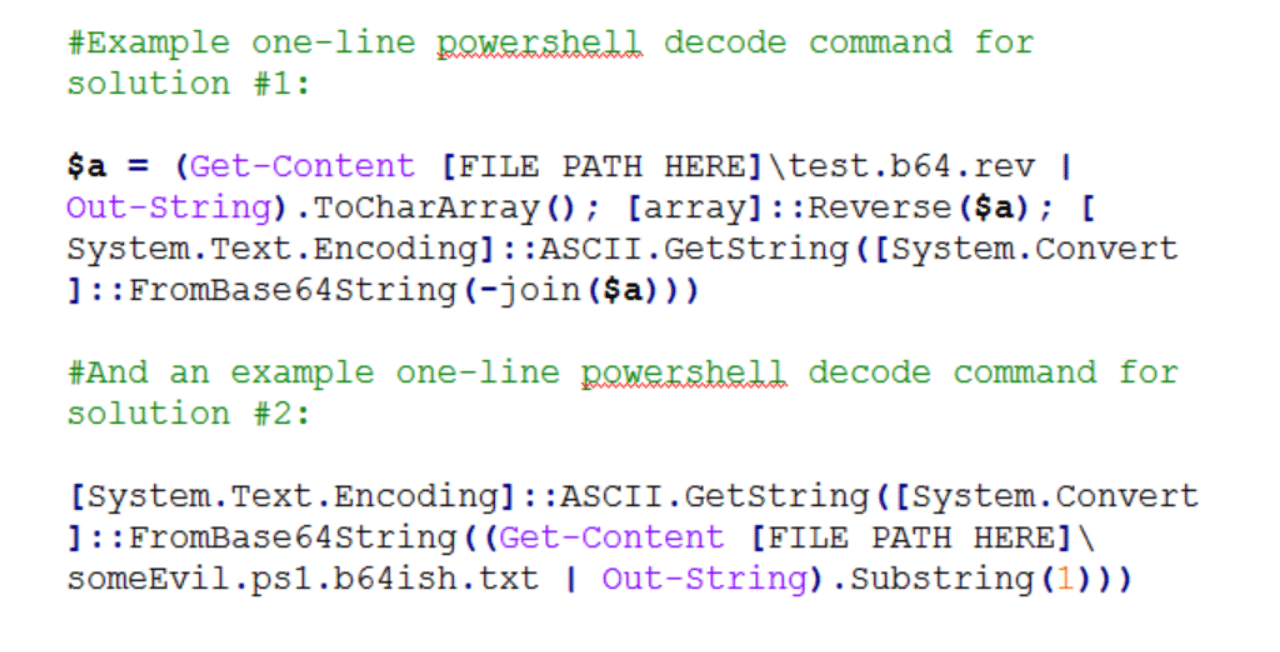
AV Avoidance – Base64’ish Obfuscation
Here’s a quick and simple anti-virus avoidance trick for malicious payloads. Background I came across the need today to avoid static/string based detection in a suite of AV products for a few powershell scripts I was staging to a box. Typically, I’d use some combination of encryption or custom, semi-complex obfuscation to get past proxy […]

Hacker’s Ethics – My Changing Perspective
Personal Ethics is not something that changes too dramatically over time. The foundation of our ethics is typically laid as children with small changes throughout our life. Untypical, then, was a major shift in my personal ethics as it relates to “security research”, aka hacking. Intro Has your spouse ever told you something a million […]

History of the Term EDR
Today I asked myself, When did the term EDR come out? It seemed to just come out of left field. What is EDR? EDR = Endpoint Detection & Response: “This name reflects the endpoint (as opposed to the network), threats (as opposed to just malware and officially declared incidents), and tools’ primary usage for both detection and […]

Exposing Tanium: A Hacker’s Paradise
Tanium has gained much popularity in the past few years. Those jumping on the Tanium train need to beware. If your company uses Tanium, your data is at high risk, IMO. Their “peer chain” model, and the lack of encryption of that data, are insecure and should not be trusted. This article is about Tanium: https://www.Tanium.com/products/ […]

Local Admin on X -> Local Admin on All?
If an attacker gains local admin on endpoint X in a corporate environment, is it safe to assume they can laterally move to any endpoint in the environment at will? Factually speaking, the answer is, no! That scenario is only true in a minority of cases. Here are a few common scenarios in which one […]

Breaking My Silence
It has been 3.5 years since I left the NSA. While working there, I could not publish anything of value. Because of all of the OpSec ingrained in me, I have shied away from publishing my research, findings, and discoveries the past few years. Attending Derbycon 2017 helped to finally break my OpSec shell. One […]
Restricting to Local Admin != Mitigation
I frequently come across and use endpoint exploits and attack vectors that “require admin”. Almost as frequently, I hear people in the industry stating, “We’re safe from that; it requires a local admin|system”. In many cases, that is not mitigation. If you’re putting trust in the assumption that restricting to local admin will protect you, […]
