BLUF Should security testing (vulnerability scanning, web app pentesting, etc.) be performed through a full protection stack (firewall, IPS, WAF, email filter, etc.), or should the tester’s IP be whitelisted? Bottom line: You are highly encouraged to whitelist the tester’s IP address from any active interference in your protection system(s). The faster we can identify […]
Category: Online Security
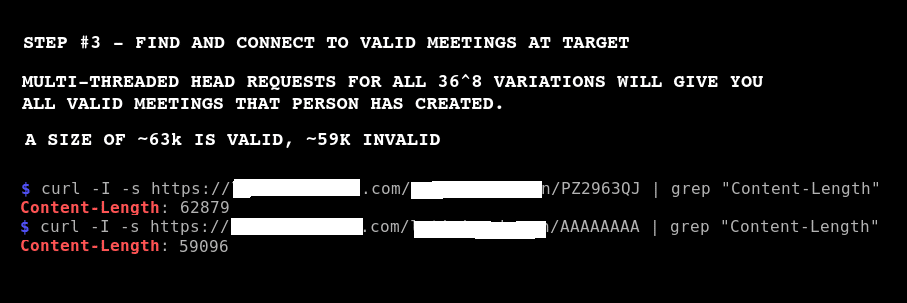
Bruteforce and Join Skype Meetings
I was able to find and join several random @SkypeBusiness meetings today… Step #1: Discover Companies Using Skype intitle:"Skype for Business Web App" "Skype for Business Web App" Step #2: Find Usernames inurl:http://example.com intitle:"skype|lync" Step #3: Bruteforce Meeting IDs Bruteforce meeting IDs to find meetings to join. Exploit is not being released at this time. […]

Enumeration Vulnerability in Leading Email Providers
Almost one-half of email providers, some of them leading providers, are vulnerable to an email/username verification attack with no apparent mitigating controls. This is my attack code and research. Pre-Req I’m not going to spend a ton of time explaining things to the nth degree. If things alluded to here don’t make sense to you, […]

I Have Your PII
I have all of your PII (Personally Identifiable Information) from your voter registration. One caveat, I only did so for one of the US Congressional Districts in Texas, but I could have just as easily obtained all voter records. This article is about what it took to obtain records and the implications. Background Recently, I […]

Binary File Patching Scripts
I am releasing code to help attackers patch their binaries on the fly to avoid checksum-based detections. As I mentioned in a previous article, https://penconsultants.com/traditional-iocs-suck/, checksum-based detections are close to worthless. But, they are still used by AV vendors, intel feeds, proxy and endpoint-based detections, etc. Defenders need to stop relying on checksum-based detections. I’m releasing […]
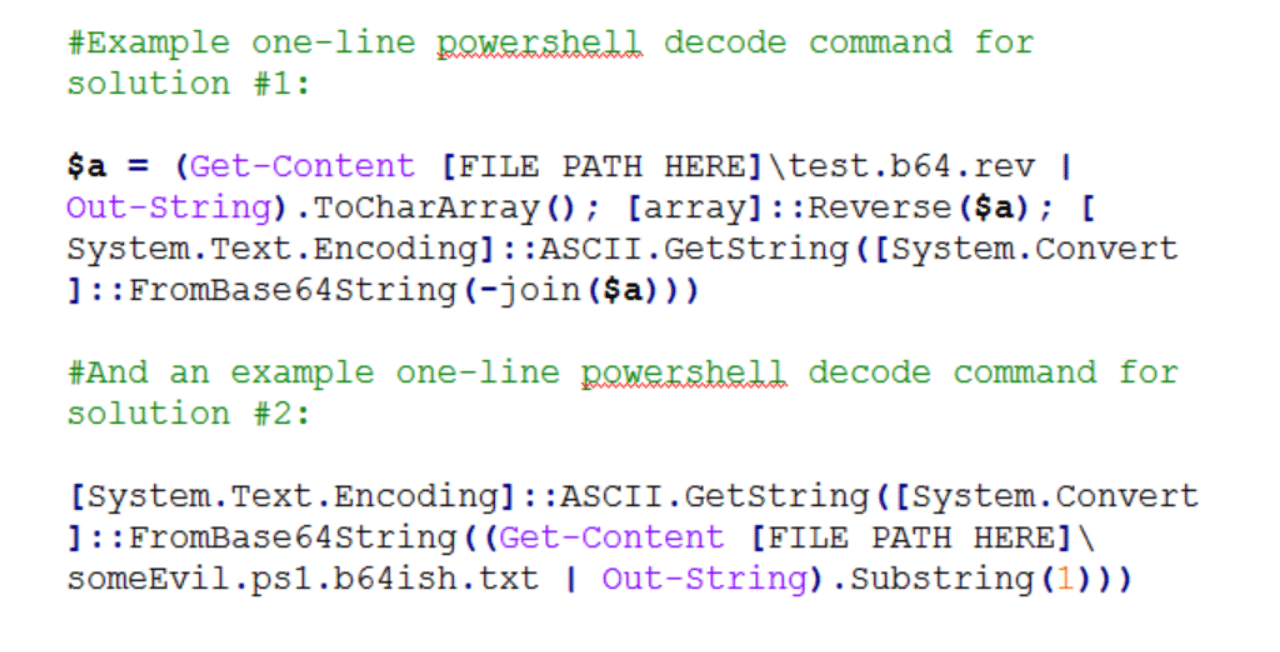
AV Avoidance – Base64’ish Obfuscation
Here’s a quick and simple anti-virus avoidance trick for malicious payloads. Background I came across the need today to avoid static/string based detection in a suite of AV products for a few powershell scripts I was staging to a box. Typically, I’d use some combination of encryption or custom, semi-complex obfuscation to get past proxy […]

Local Admin on X -> Local Admin on All?
If an attacker gains local admin on endpoint X in a corporate environment, is it safe to assume they can laterally move to any endpoint in the environment at will? Factually speaking, the answer is, no! That scenario is only true in a minority of cases. Here are a few common scenarios in which one […]
Restricting to Local Admin != Mitigation
I frequently come across and use endpoint exploits and attack vectors that “require admin”. Almost as frequently, I hear people in the industry stating, “We’re safe from that; it requires a local admin|system”. In many cases, that is not mitigation. If you’re putting trust in the assumption that restricting to local admin will protect you, […]

Crown Jewels: Monitoring vs Mitigating
There are many defenses one can build to protect and monitor systems in the cyber world. More times than not, one would monitor for a certain type of behavior, but not block (i.e. alert only). Most typically, this is due to the fact that it might be difficult to have enough fidelity in the detection to distinguish between good […]

Password Hash-Like Password
If you don’t think a password hash is just as good as getting a plaintext password (99% of the time), then you should read this. Several of my clients in the past have downplayed my findings related to the discovery of password hashes, even after I cracked them. This article, like many of my articles, […]