I recently had the privilege to perform full scope application security testing against 1E’s Tachyon, an endpoint incident response and remediation platform. I was so impressed with it, I sought (and received) approval from 1E to release this article publicly, detailing my impressions. Earlier this year, 1E and I began dialoguing about the possibility of evaluating […]
Year: 2018

Binary File Patching – Echo Command
Here is a single line Windows batch command which renames and patches a binary in order to avoid detection. The Problem Many detections that look for malicious or uncommon usage of built-in Windows tools/utilities (i.e. attackers living-of-the-land) depend on well-known file/process names (ex. powershell.exe). But, if defenders are also monitoring for the well known checksums […]

Burp+SSLintercept with Kali+Docker+Java+Python+Browser
I couldn’t find a single source for setting this up, so I thought I would copy/paste my notes for others to reference. Feedback appreciated. The goal is to proxy all http-80 and https-443 traffic in a docker/OS stack through Burp with (trusted) SSL intercept. My Environment: Notes: The Steps – Host OS: Install Burp from […]
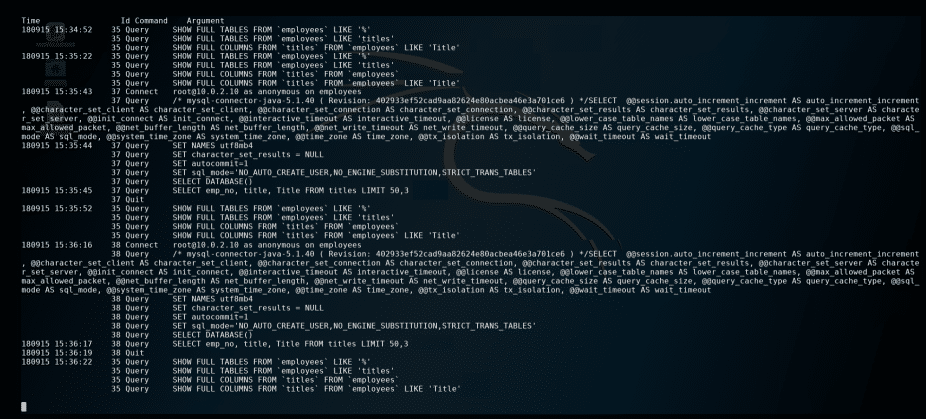
Passwords in DB Logs
This was useful (for an attacker) when password hashing (during authentication) was being performed at the DB level. Background Having access to a DB with encrypted (and salted) password hashes can still present a challenge to recovering a significant percentage of the cleartext passwords. Sure, one will be able to crack some using a decent […]
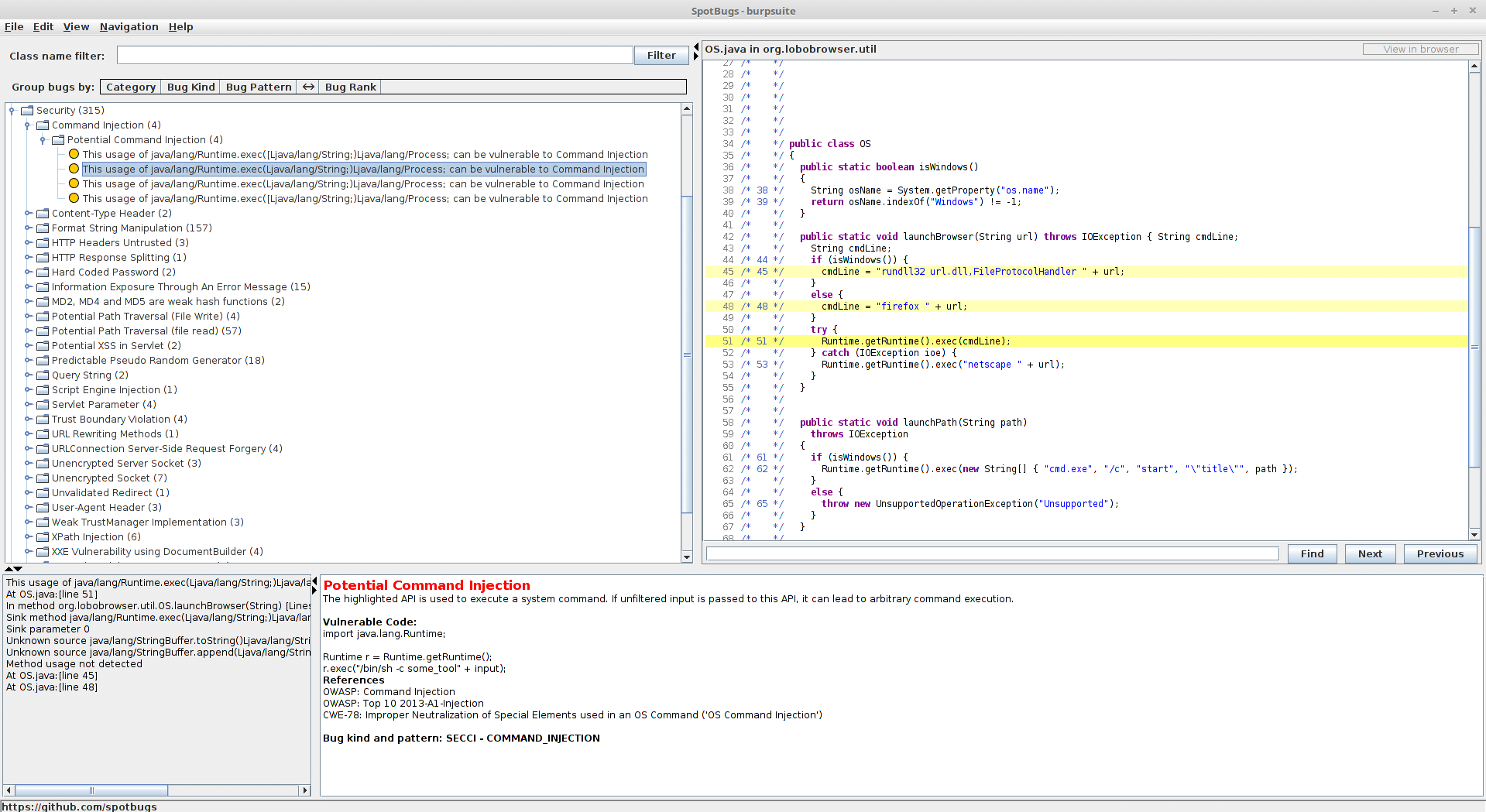
Finding Vulns in JARs with Spotbugs
How to find security vulnerabilities in JARs with SpotBugs… [Note: burpsuite is just being used as an example] Spotbugs is awesome. But, the instructions for compiling it and running as a standalone app were not that clear to me. Because of this, I decided to put together the rather simple steps below. Prerequisites Decompile the […]
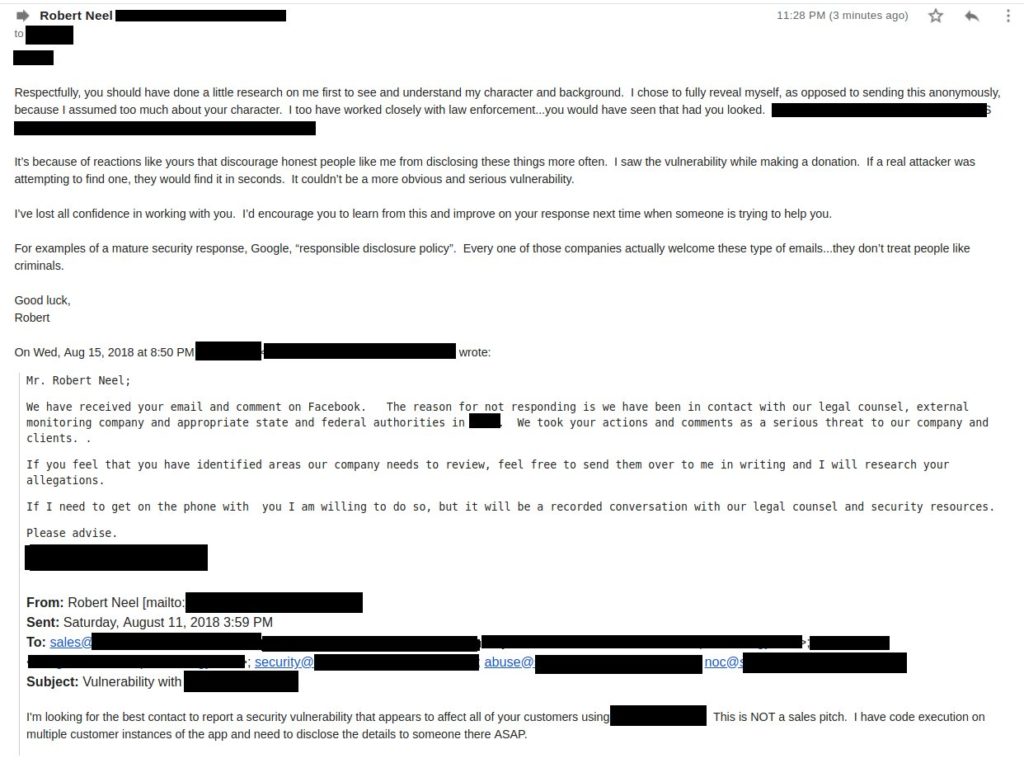
A Vulnerability Disclosure Gone Wrong
An example of a vulnerability disclosure gone wrong… Background I debated mentioning the company but will resist. While making a contribution through a well-known payment processing app, I discovered a vulnerability. It was an OWASP top-10 vulnerability and was discoverable while doing nothing more than using the app as a normal-ish user would. Okay, true, […]
Shields Down Security Testing
BLUF Should security testing (vulnerability scanning, web app pentesting, etc.) be performed through a full protection stack (firewall, IPS, WAF, email filter, etc.), or should the tester’s IP be whitelisted? Bottom line: You are highly encouraged to whitelist the tester’s IP address from any active interference in your protection system(s). The faster we can identify […]

My Disclosure Process
Here are my disclosure processes and guidelines. This is for those discoveries which seem to just fall in my lap while causally using and/or seeing a product. My disclosure process is an attempt to do the right thing when this happens. Note: NDA-protected discoveries (ex. through a client engagement) would not be subject to this. My […]
Create a macOS High Sierra VM
After struggling for many hours to get macOS (High Sierra) running in a VM (Virtualbox) on a Linux host (Ubuntu/Mint), I finally succeeded. Although there were dozens of really good tutorials on the topic, none of them were a 100% solution to my specific situation. Here’s what I did to get it working. Notes: Step […]
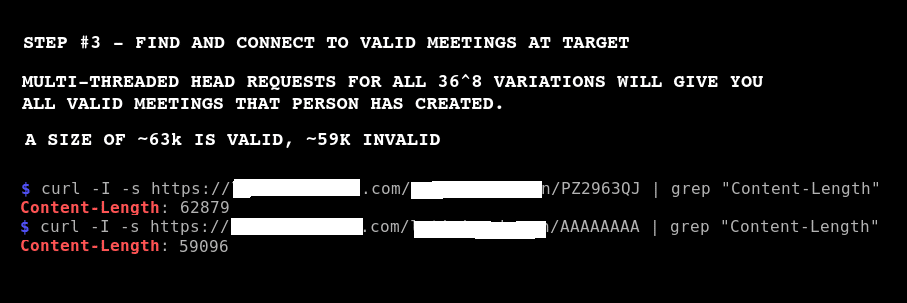
Bruteforce and Join Skype Meetings
I was able to find and join several random @SkypeBusiness meetings today… Step #1: Discover Companies Using Skype intitle:”Skype for Business Web App” “Skype for Business Web App” Step #2: Find Usernames inurl:http://example.com intitle:”skype|lync” Step #3: Bruteforce Meeting IDs Bruteforce meeting IDs to find meetings to join. Exploit is not being released at this time. […]

