I’m often asked questions such as, “How do I get into Cybersecurity?” or “How do I get from an IT role a cybersecurity role?”. This is a copy/paste, with a few edits, from previous emails. Bottom Line up Front (BLUF) I’d lean towards a shorter/cheaper tech degree in the field you want to go into […]
Category: Tips & Tricks
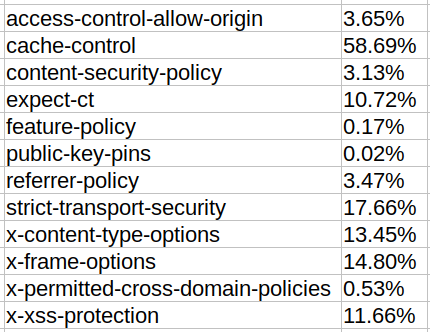
HTTP Response Headers
While preparing for a monthly Lunch-and-Learn lesson for a client, I wanted to collect various examples of good, bad, faulty, and missing HTTP response headers. As is typical, I went a little overboard and collected all of the headers for the top one million websites. This article will describe some interesting findings and the raw […]

Forced Password Rotation == Incrementing
Some organizations still force a user to change their password at a defined interval. This is not only ineffective, but it is also detrimental to the security of users’ accounts. This is a follow-up to another article we wrote last year, A Sensible Password Policy. It might be beneficial to review it first if you haven’t […]

MFA – Without the FUD
Ditch SMS-based MFA now – it’s no better than single factor authentication! Have you seen headlines similar to this recently? A tip: Follow the money. The majority of those articles are paid advertisements for a hardware or software based MFA solution. Here’s an non-vendor biased opinion from the perspective of an attacker who has contended with […]

Selecting a Reputable Security Testing Company
When choosing a security testing company to perform penetration testing, red teaming, etc., there are a few things you should consider to guarantee that you find the optimal company for your situation. Transparency: If you can’t answer all, or nearly all, of the following from the company’s website, they are not transparent. Company Size: Size […]
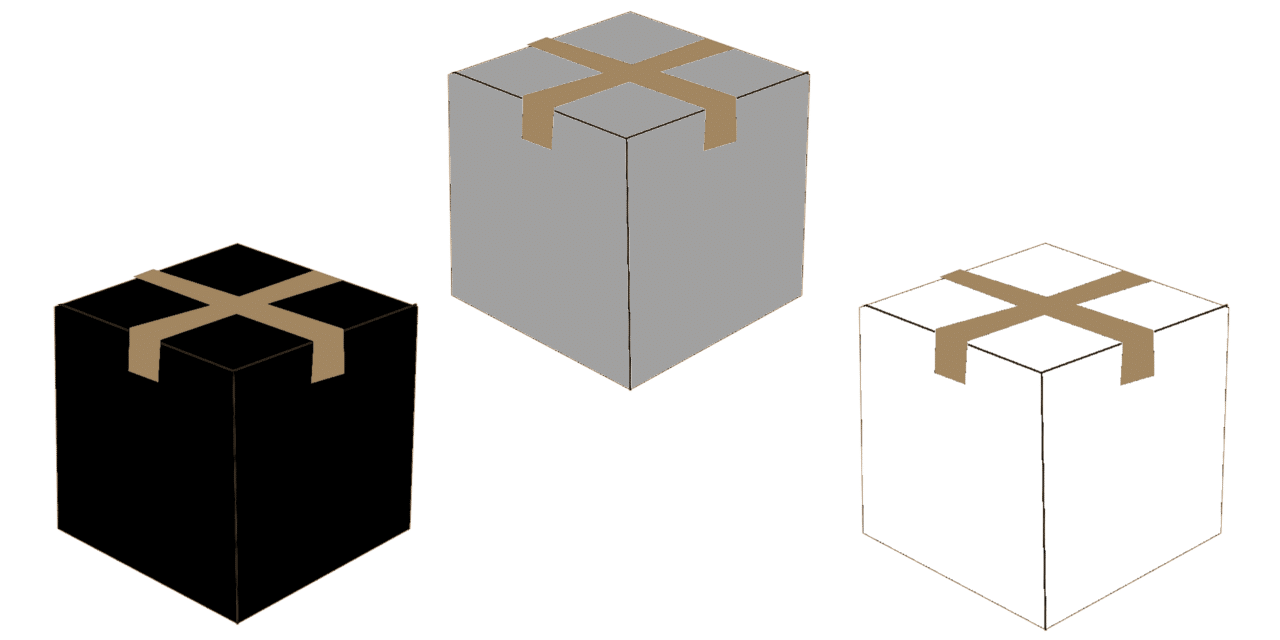
Gray Box vs. Black Box vs. White Box Testing
The balance of white/black box security testing is a decision you will ultimately make based on your budget, risk concerns, internal policies, and possibly compliance requirements. This article is intended to help a client think through the benefits of white box testing and the downsides to full black box testing, as well as provide several […]
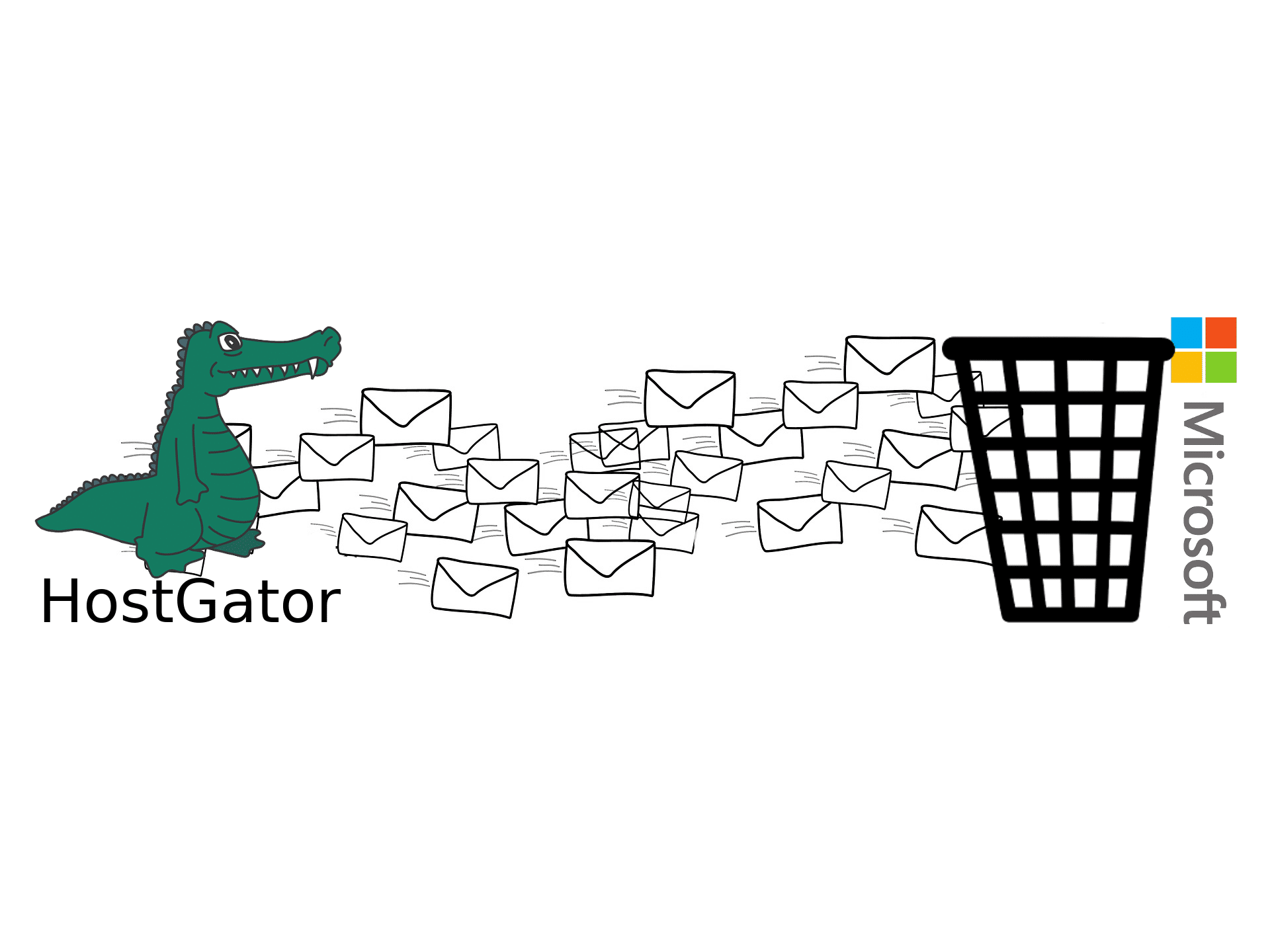
Troublesome: HostGator and Microsoft
This article is to inform you of the incompatibility that exists between HostGator and Microsoft-hosted email services, Microsoft’s inability to accurately distinguish good email from spam, and how unhelpful they both have been in resolving the issue. I hope this article will help inform two groups of people: (1) those currently using/those considering using any […]

A Sensible Password Policy
A password should be 24+ characters, require lowercase, uppercase, numbers, special characters, not one of the last 24 passwords, not more than three characters in a row of the same type, and change every 30 days. Uh, NOT! Here’s a more sensible policy. The policy described in the intro is a real policy in some […]

Binary File Patching – Echo Command
Here is a single line Windows batch command which renames and patches a binary in order to avoid detection. The Problem Many detections that look for malicious or uncommon usage of built-in Windows tools/utilities (i.e. attackers living-of-the-land) depend on well-known file/process names (ex. powershell.exe). But, if defenders are also monitoring for the well known checksums […]

Burp+SSLintercept with Kali+Docker+Java+Python+Browser
I couldn’t find a single source for setting this up, so I thought I would copy/paste my notes for others to reference. Feedback appreciated. The goal is to proxy all http-80 and https-443 traffic in a docker/OS stack through Burp with (trusted) SSL intercept. My Environment: Notes: The Steps – Host OS: Install Burp from […]