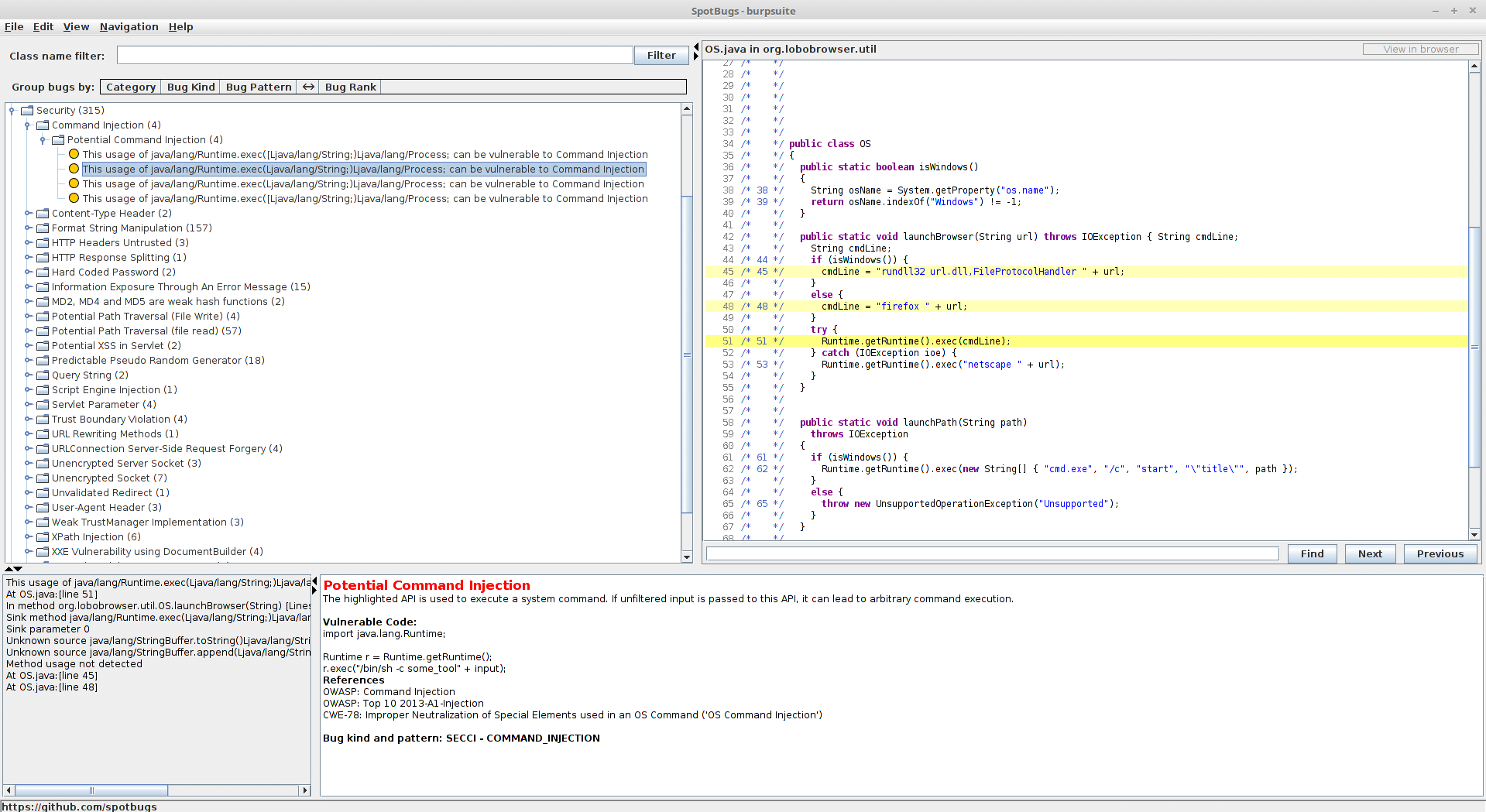
How to find security vulnerabilities in JARs with SpotBugs… [Note: burpsuite is just being used as an example] Spotbugs is awesome. But, the instructions for compiling it and running as a standalone app were not that clear to me. Because of this, I decided to put together the rather simple steps below. Prerequisites Decompile the […]
Blog
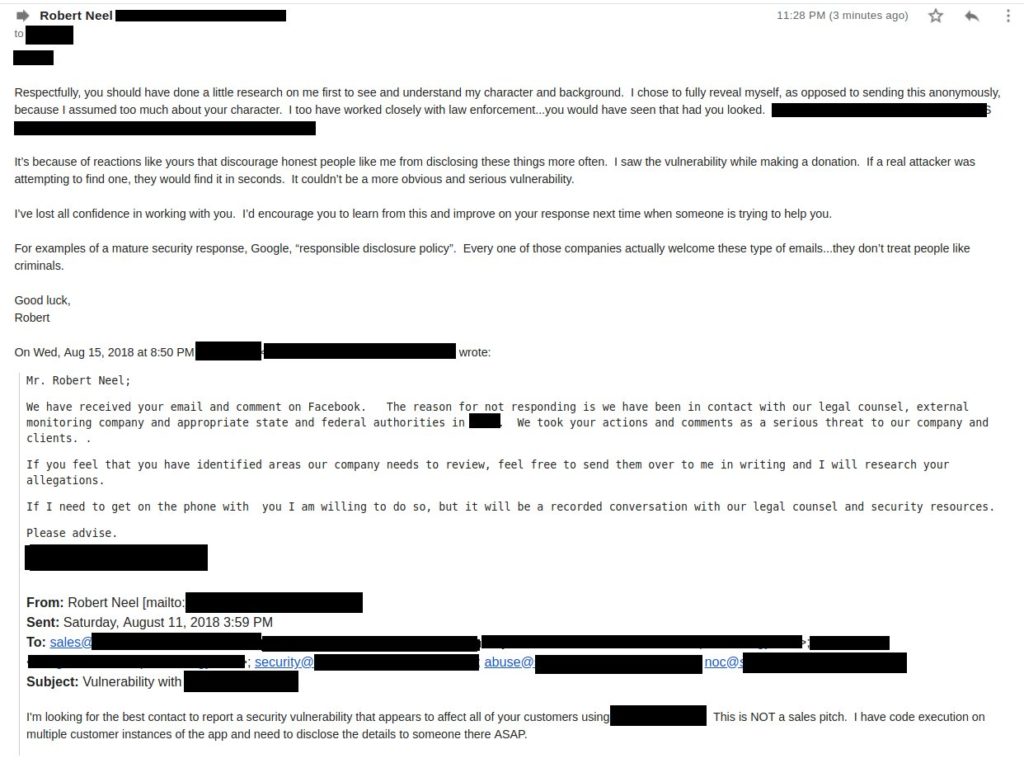
A Vulnerability Disclosure Gone Wrong
An example of a vulnerability disclosure gone wrong… Background I debated mentioning the company but will resist. While making a contribution through a well-known payment processing app, I discovered a vulnerability. It was an OWASP top-10 vulnerability and was discoverable while doing nothing more than using the app as a normal-ish user would. Okay, true, […]
Shields Down Security Testing
BLUF Should security testing (vulnerability scanning, web app pentesting, etc.) be performed through a full protection stack (firewall, IPS, WAF, email filter, etc.), or should the tester’s IP be whitelisted? Bottom line: You are highly encouraged to whitelist the tester’s IP address from any active interference in your protection system(s). The faster we can identify […]

My Disclosure Process
Here are my disclosure processes and guidelines. This is for those discoveries which seem to just fall in my lap while causally using and/or seeing a product. My disclosure process is an attempt to do the right thing when this happens. Note: NDA-protected discoveries (ex. through a client engagement) would not be subject to this. My […]
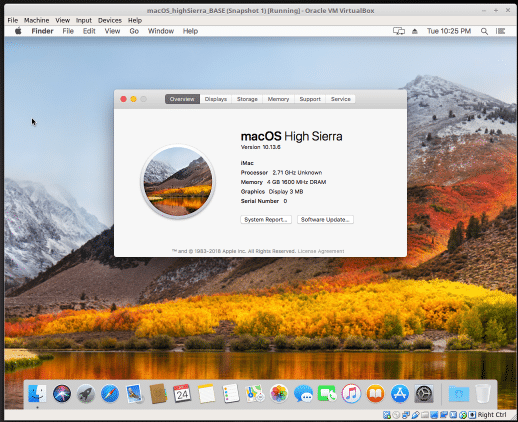
Create a macOS High Sierra VM
After struggling for many hours to get macOS (High Sierra) running in a VM (Virtualbox) on a Linux host (Ubuntu/Mint), I finally succeeded. Although there were dozens of really good tutorials on the topic, none of them were a 100% solution to my specific situation. Here’s what I did to get it working. Notes: Step […]
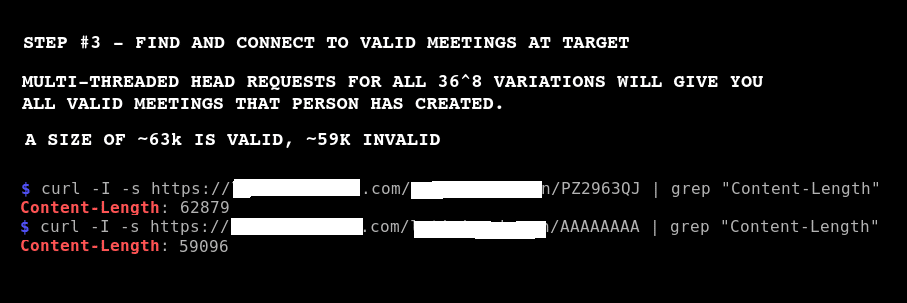
Bruteforce and Join Skype Meetings
I was able to find and join several random @SkypeBusiness meetings today… Step #1: Discover Companies Using Skype intitle:"Skype for Business Web App" "Skype for Business Web App" Step #2: Find Usernames inurl:http://example.com intitle:"skype|lync" Step #3: Bruteforce Meeting IDs Bruteforce meeting IDs to find meetings to join. Exploit is not being released at this time. […]

Presentation: Zero to Hero – A Red Team’s Journey
On 16 June 2018, David and I presented “Zero to Hero – A Red Team’s Journey” at BSides SATX. Here are links to the slide deck, audience handout, and video recording. Slides and handout: https://drive.google.com/drive/folders/12nsWBaqhgukMEn4MwKXsv2LwQF3kmD2U Video recording: https://youtu.be/lF4uOKjQyuk

Presentation: Zero to Hero – Building a Red Team
On 23 March 2018, David and I presented “Zero to Hero – Building a Red Team, One Step at a Time” at HackWest in Salt Lake City. Here are links to the slide deck, audience handout, and video recording. Slides and handout: https://drive.google.com/open?id=1daaIUFEQLSesZ34ar_YbJS0a6u91JtxM Video recording: https://youtu.be/LLdaM0afKUU

Enumeration Vulnerability in Leading Email Providers
Almost one-half of email providers, some of them leading providers, are vulnerable to an email/username verification attack with no apparent mitigating controls. This is my attack code and research. Pre-Req I’m not going to spend a ton of time explaining things to the nth degree. If things alluded to here don’t make sense to you, […]

I Have Your PII
I have all of your PII (Personally Identifiable Information) from your voter registration. One caveat, I only did so for one of the US Congressional Districts in Texas, but I could have just as easily obtained all voter records. This article is about what it took to obtain records and the implications. Background Recently, I […]