This article will demonstrate how to perform a mass collection of all phone records in an enterprise from many popular series of Cisco IP Phones and how to prevent it. Many of the Cisco IP Phone series have a built-in web server that allows users and admins to “view the phone statistics and modify some […]
Category: Miscellaneous
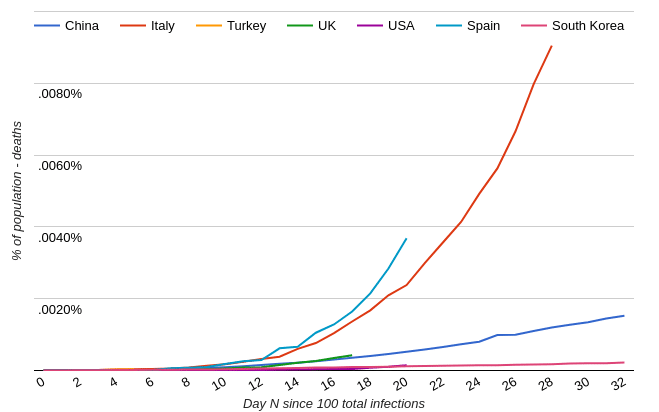
Coronavirus
The Coronavirus outbreak should be taken for what it is, an outbreak that deserves our attention and precautionary measures, but not panic. Notes: A web search similar to “[your country] coronavirus trajectory” will reveal news articles and charts that make it seem the world is coming to an end. Here is an example chart used […]

Paired Visitor/Escort Proximity Badges
How confident are you that visitors within your organization are constantly supervised by an employee? How often does an employee fail to properly hand off their escort duties to another employee? This is a solution we came up in response to a recent physical Social Engineering Assessment we preformed for a client. It is an all too […]
Presentation: RATs Without Borders
This presentation, “RATs Without Borders – Moving Your Cheese”, was presented on 29 March 2019 at BSidesATX. Slides: BSides_ATX_2019.pdf Gitlab: https://gitlab.com/J35u5633k/RATsWithoutBorders_public Video recording: https://www.youtube.com/watch?v=ZubIQfHEUzA Original event details: https://bsidesaustin2019.sched.com/event/M5yt/rats-without-borders-moving-your-cheese Description: Antivirus solutions continue to fail us. This talk will highlight my research on the effectiveness of the leading AV solutions. The overall strategy is to create a RAT in every […]

Presentation: Zero to Hero – A Red Team’s Journey
On 16 June 2018, David and I presented “Zero to Hero – A Red Team’s Journey” at BSides SATX. Here are links to the slide deck, audience handout, and video recording. Slides and handout: https://drive.google.com/drive/folders/12nsWBaqhgukMEn4MwKXsv2LwQF3kmD2U Video recording: https://youtu.be/lF4uOKjQyuk

Presentation: Zero to Hero – Building a Red Team
On 23 March 2018, David and I presented “Zero to Hero – Building a Red Team, One Step at a Time” at HackWest in Salt Lake City. Here are links to the slide deck, audience handout, and video recording. Slides and handout: https://drive.google.com/open?id=1daaIUFEQLSesZ34ar_YbJS0a6u91JtxM Video recording: https://youtu.be/LLdaM0afKUU

Sex Objects
Is it acceptable for a male to walk up to a female coworker and say, “You’ve got a booty like a Cadillac”? What about singing, to the same co-worker, “Come to the back seat of my car and I’ll let you have it”? I think most would agree these would not be acceptable. How is […]

Hacker’s Ethics – My Changing Perspective
Personal Ethics is not something that changes too dramatically over time. The foundation of our ethics is typically laid as children with small changes throughout our life. Untypical, then, was a major shift in my personal ethics as it relates to “security research”, aka hacking. Intro Has your spouse ever told you something a million […]

History of the Term EDR
Today I asked myself, When did the term EDR come out? It seemed to just come out of left field. What is EDR? EDR = Endpoint Detection & Response: “This name reflects the endpoint (as opposed to the network), threats (as opposed to just malware and officially declared incidents), and tools’ primary usage for both detection and […]

Breaking My Silence
It has been 3.5 years since I left the NSA. While working there, I could not publish anything of value. Because of all of the OpSec ingrained in me, I have shied away from publishing my research, findings, and discoveries the past few years. Attending Derbycon 2017 helped to finally break my OpSec shell. One […]

