Here’s a look at the results from our recent effort analyzing GraphQL API endpoints across the web, and the percentage of those endpoints that allowed an unauthenticated user to view the query & data schema. The intent of this article is to address the implications of allowing this schema to be retrieved, similar technologies that […]
Year: 2020

Building a Security Testing Business
I am often asked, “How did you get started with your security testing business?” “What are some lessons learned?” “What are your current challenges?” I have been asked enough times that I decided to post my thoughts in blog format. How did you decide it was the right time to take the step from W-2 […]
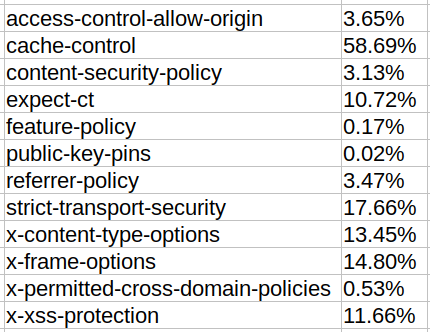
HTTP Response Headers
While preparing for a monthly Lunch-and-Learn lesson for a client, I wanted to collect various examples of good, bad, faulty, and missing HTTP response headers. As is typical, I went a little overboard and collected all of the headers for the top one million websites. This article will describe some interesting findings and the raw […]

MFA Implementation Attacks
Most Multi-Factor-Authentication (MFA) implementations do not protect your password from brute forcing or from account level DoS attacks. This article will demonstrate various attacks that exploit weaknesses found in nearly every industry Identity and Access Management (IAM) provider/solution as well as offer solutions on how to mitigate. Note: This article builds on the previously released https://penconsultants.com/blog/tips-tricks/mfa-without-the-fud/ […]

Mass Call Record Collection – Cisco IP Phones
This article will demonstrate how to perform a mass collection of all phone records in an enterprise from many popular series of Cisco IP Phones and how to prevent it. Many of the Cisco IP Phone series have a built-in web server that allows users and admins to “view the phone statistics and modify some […]
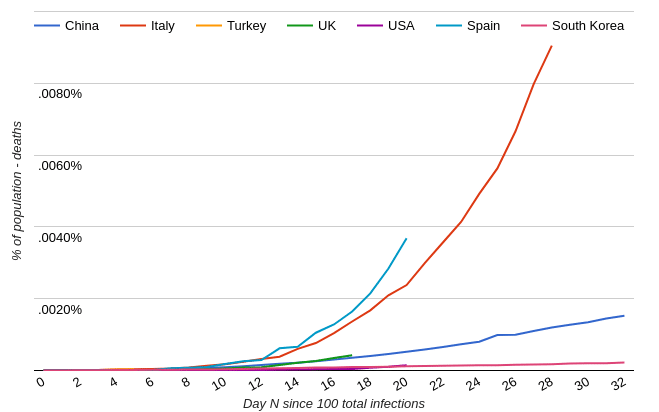
Coronavirus
The Coronavirus outbreak should be taken for what it is, an outbreak that deserves our attention and precautionary measures, but not panic. Notes: A web search similar to “[your country] coronavirus trajectory” will reveal news articles and charts that make it seem the world is coming to an end. Here is an example chart used […]

Forced Password Rotation == Incrementing
Some organizations still force a user to change their password at a defined interval. This is not only ineffective, but it is also detrimental to the security of users’ accounts. This is a follow-up to another article we wrote last year, A Sensible Password Policy. It might be beneficial to review it first if you haven’t […]

MFA – Without the FUD
Ditch SMS-based MFA now – it’s no better than single factor authentication! Have you seen headlines similar to this recently? A tip: Follow the money. The majority of those articles are paid advertisements for a hardware or software based MFA solution. Here’s an non-vendor biased opinion from the perspective of an attacker who has contended with […]