The balance of white/black box security testing is a decision you will ultimately make based on your budget, risk concerns, internal policies, and possibly compliance requirements. This article is intended to help a client think through the benefits of white box testing and the downsides to full black box testing, as well as provide several […]
Blog
Troublesome: HostGator and Microsoft
This article is to inform you of the incompatibility that exists between HostGator and Microsoft-hosted email services, Microsoft’s inability to accurately distinguish good email from spam, and how unhelpful they both have been in resolving the issue. I hope this article will help inform two groups of people: (1) those currently using/those considering using any […]
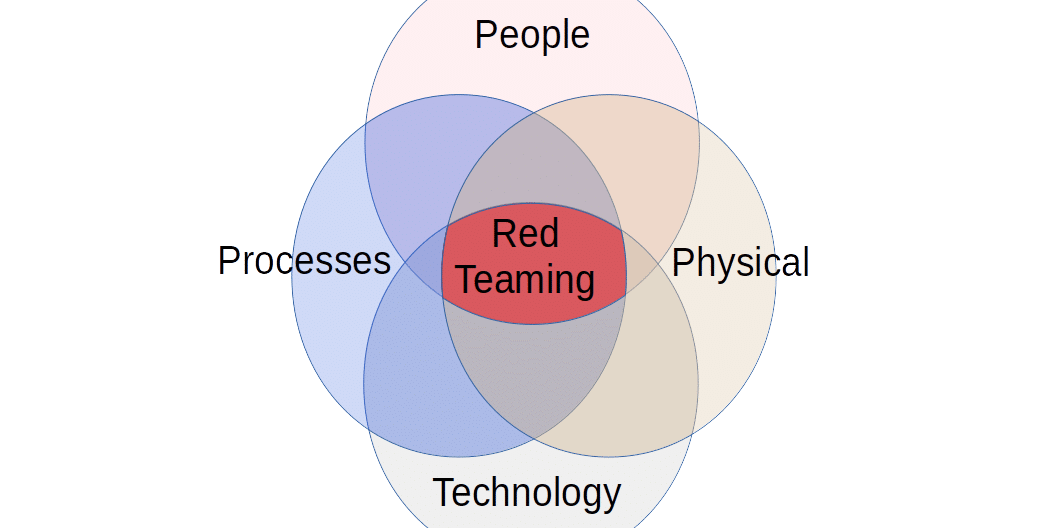
Red Teaming vs Penetration Testing vs Vulnerability Scanning vs Vulnerability Assessments
What is the difference between “Vulnerability Scanning”, “Vulnerability Assessments”, “Penetration Testing”, and “Red Teaming”? What do they mean? Which one do you need performed on your systems? The industry is very opinionated on the definitions of these four terms. This article will share our view of the similarities and differences between vulnerability scanning (vuln scan), […]
Presentation: RATs Without Borders
This presentation, “RATs Without Borders – Moving Your Cheese”, was presented on 29 March 2019 at BSidesATX. Slides: BSides_ATX_2019.pdf Gitlab: https://gitlab.com/J35u5633k/RATsWithoutBorders_public Video recording: https://www.youtube.com/watch?v=ZubIQfHEUzA Original event details: https://bsidesaustin2019.sched.com/event/M5yt/rats-without-borders-moving-your-cheese Description: Antivirus solutions continue to fail us. This talk will highlight my research on the effectiveness of the leading AV solutions. The overall strategy is to create a RAT in every […]

Threat Intelligence and Brand Monitoring
One thing that nearly every department in your organization is concerned with is monitoring for references to your organization on the internet, such as brand reputation, cybersecurity threats, intellectual property rights, threats of harm against life or property, etc. But, what are your options? [This is a work in progress in which we intend to […]

A Sensible Password Policy
A password should be 24+ characters, require lowercase, uppercase, numbers, special characters, not one of the last 24 passwords, not more than three characters in a row of the same type, and change every 30 days. Uh, NOT! Here’s a more sensible policy. The policy described in the intro is a real policy in some […]

Tachyon – A Security Pros Paradise
I recently had the privilege to perform full scope application security testing against 1E’s Tachyon, an endpoint incident response and remediation platform. I was so impressed with it, I sought (and received) approval from 1E to release this article publicly, detailing my impressions. Earlier this year, 1E and I began dialoguing about the possibility of evaluating […]

Binary File Patching – Echo Command
Here is a single line Windows batch command which renames and patches a binary in order to avoid detection. The Problem Many detections that look for malicious or uncommon usage of built-in Windows tools/utilities (i.e. attackers living-of-the-land) depend on well-known file/process names (ex. powershell.exe). But, if defenders are also monitoring for the well known checksums […]

Burp+SSLintercept with Kali+Docker+Java+Python+Browser
I couldn’t find a single source for setting this up, so I thought I would copy/paste my notes for others to reference. Feedback appreciated. The goal is to proxy all http-80 and https-443 traffic in a docker/OS stack through Burp with (trusted) SSL intercept. My Environment: Notes: The Steps – Host OS: Install Burp from […]
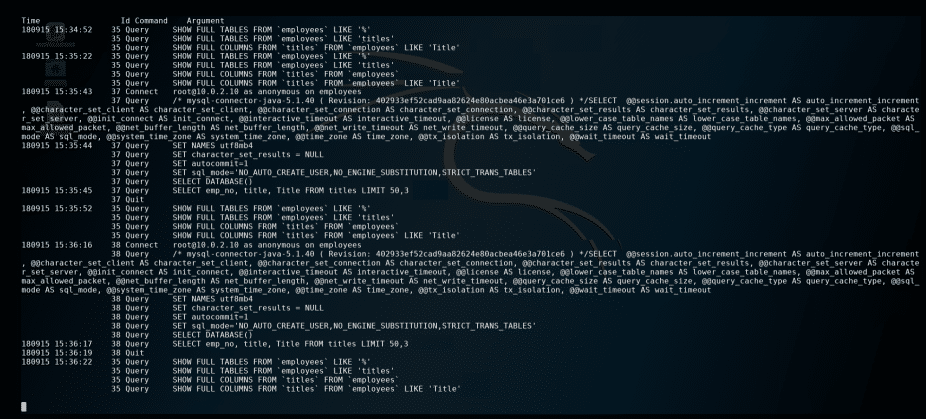
Passwords in DB Logs
This was useful (for an attacker) when password hashing (during authentication) was being performed at the DB level. Background Having access to a DB with encrypted (and salted) password hashes can still present a challenge to recovering a significant percentage of the cleartext passwords. Sure, one will be able to crack some using a decent […]